Bridging Policy and Practice: My Summer with SANS Singapore
Bridging Policy and Practice: My Summer with SANS Singapore

This summer, I had the privilege of interning with the SANS Institute’s Singapore office. SANS founded the Global Information Assurance Certification (GIAC) in 1999 to establish rigorous, standardized credentials for the cybersecurity industry, and has since become the world’s largest provider of cybersecurity training and research. Today, GIAC certifications are widely regarded as the “gold standard” of cyber security knowledge and skill, and SANS works with government agencies and private firms worldwide to train and certify their cybersecurity professionals.
In Singapore, SANS works closely with the Cyber Security Agency (CSA) to improve the country’s cyber resilience through training, capacity building and running national-level cyber exercises. My primary assignment at SANS Singapore was to run exercise control for one such exercise – namely, Exercise CyberStar (XCS), Singapore’s biennial national cybersecurity crisis management exercise that was jointly organized by SANS and CSA. After spending most of my career working in security policy and analysis, this was a rare opportunity for me to experience the operational side of cybersecurity first hand.
The 2025 edition of XCS was Singapore’s largest and most intensive exercise to date, and involved nearly 500 participants from CSA, critical information infrastructure operators, the Singapore Armed Forces’ Digital and Intelligence Service and other government agencies overseeing key national sectors like healthcare, transport and media. Over 11 days, participants were tested on scenarios based on key threats observed in the global cyber landscape, such as Advanced Persistent Threats (APTs) and attacks on critical systems that spilled over into multiple other sectors. The exercise concluded in a SANS-conducted Industrial Control Systems (ICS) NetWars tournament, with participants forming teams to compete in a capture-the-flag (CTF) exercise that tested their understanding of key ICS systems.
My role in Exercise Control primarily involved creating exercise “injects” that simulated realistic developments and pressures for the exercise participants. These included mock Telegram threats from hacktivist groups, spearphishing emails, ransomware screens and cyber intelligence reports. As participants responded to the pre-determined exercise scenario, I also created unplanned, or “dynamic” injects that simulated the effects of their actions on Singaporean public opinion.
In order to create realistic public reaction injects on demand and at scale, I coded a GPT wrapper that generated social media content in formats similar to several major social media platforms. I was particularly proud of this project as it challenged and stretched both my technical skills and my capacity to think creatively about AI tools – while I had a light coding background prior to working at SANS, I had only ever used it to work on hobbyist projects and never in the workplace.
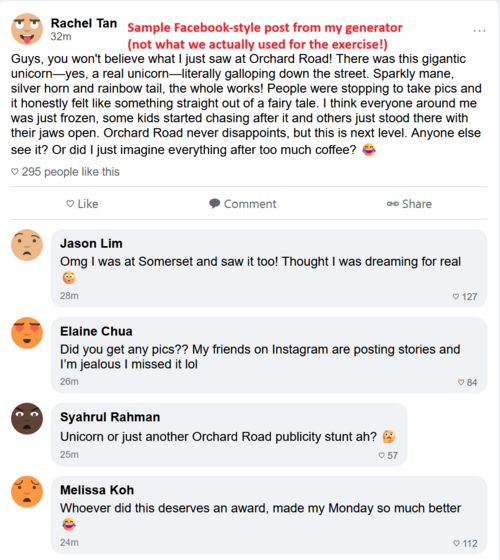
I found two technical problems especially challenging:
- Designing HTML templates that accurately mimicked the look and feel of platforms like Facebook, Reddit and Twitter. As I had no prior experience with HTML, I relied heavily on vibe coding tools like Copilot to help fill this knowledge gap, which ended up teaching me a lot about their strengths and limitations.
- Using the Structured Outputs function of OpenAI’s Responses API. This helped significantly with generating predictable outputs that could be fed into relevant parts of the HTML template, but required me to learn how to use tools like Pydantic to define custom object schema.
- (I’ve posted an open source version of the wrapper on my personal Github - you might find it useful if you’re also involved in exercise planning, model UN or any form of current affairs roleplay.)
Beyond XCS, I helped moderate SANS training courses like ICS410 (ICS/SCADA Security Essentials) and conducted interviews and data analysis for a comprehensive SANS-led review of Singapore’s national cyber exercises. (The R skills I picked up during my first year at MIP proved particularly helpful for the latter task!)
The clearest lesson I took away from my 10-week long internship was that policy professionals do need hands-on technical experience to be effective at their job. While I don’t think it's realistic to expect every policymaker to also be a professional cyber operator, they at least need a grounding in the tools and practices of the trade so that the policies they shape actually map onto how cyber defence is practiced day to day.
I plan to put this lesson into practice over the coming academic year. First, while developing tools for XCS pushed me to pick up new coding skills on the fly, it also revealed some important gaps in my foundational knowledge of object-oriented programming. I plan to take a structured coding class to address these gaps and shore up my fundamental understanding of computer science.
Second, I hope to pursue an entry-level GIAC certification myself. While the technical knowledge required to operate in the cyber world initially seemed very intimidating, moderating SANS courses showed me that with persistence I too could probably pick up and apply some of these skills – taking part in the end-of-class exercises showed me that, while I still have plenty to learn, I could actually keep pace with some of the operational professionals in the room.
Finally, I would like to thank my good friend and supervisor Matthias Chia for giving me the opportunity to work at SANS, my buddy Shyh Horng Lee for showing me the ropes, and all the staff and trainers at SANS and CSA I had the privilege of working with. Most importantly, I am thankful for the generous funding provided by FSI, without which this internship would not have been possible.

